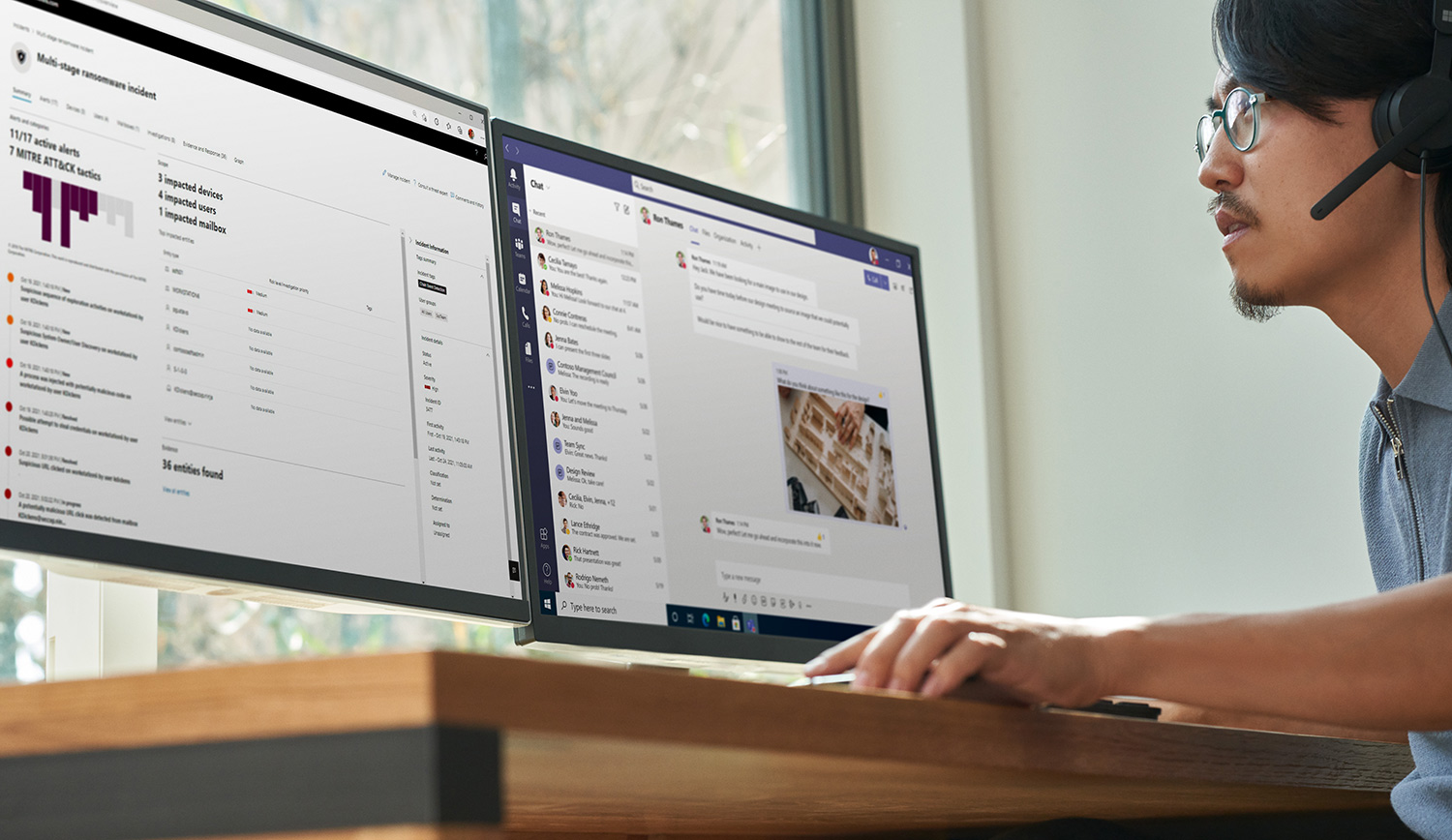
The Microsoft 365 A5 security suite helps districts and schools provide safe and secure learning experiences backed by world class protection and consolidated into one cost-effective solution. Together, the A5 security suite is crucial in helping to preserve student data, manage compliance policies, and detect and respond to cybersecurity threats.
Explore 10 Microsoft 365 A5 tools and features that can help secure your district and keep it protected.
1. Detect advanced threats with Microsoft Defender for Endpoint
When vulnerabilities are identified and pursued before they become a threat, student learning can remain uninterrupted, and all facets of an institution can continue to operate. Microsoft Defender for Endpoint is a security platform designed to protect enterprise networks from advanced threats using a combination of technology built into Windows 11 and Microsoft's cloud service. It uses endpoint behavioral sensors, cloud security analytics, and threat intelligence to detect and respond to advanced threats.
2. Prevent phishing attacks with Microsoft Defender
Phishing attacks can happen to anyone within a school or district. Microsoft 365 Defender provides multi-tiered phishing prevention that helps protect users from increasingly complex phishing attacks. Within Defender, default settings protect users from the start and IT staff can fine tune settings such as Spoof, Impersonation, and Advanced Phishing Thresholds. Schools can also refine and improve their protection through simulating attacks on individuals or groups within Active Directory or through Breach and Attack Simulation.
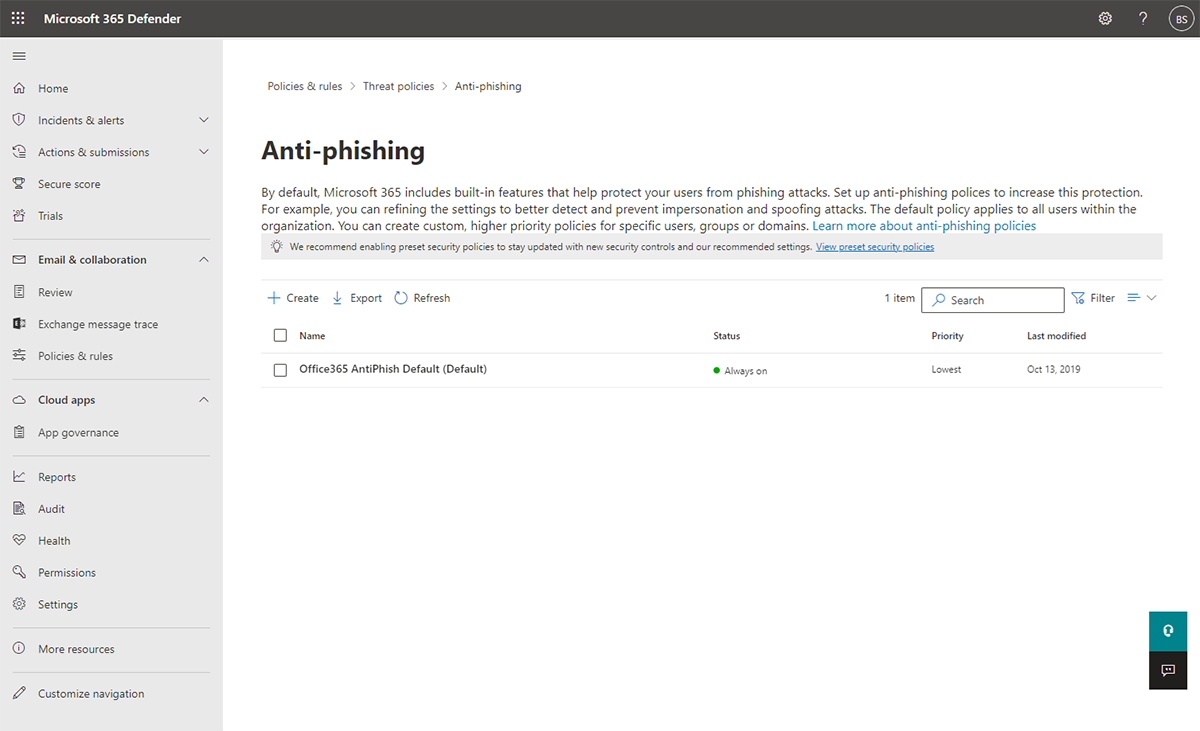
Configure Anti-Phishing settings
3. Protect users from malware with Microsoft Defender
Malware is a huge concern for schools. In fact, over 80% of reported malware attacks in the past 30 days occurred in education. Microsoft Defender contains a security feature that helps schools protect against malware, including viruses, ransomware, and spyware. It runs continuously in real-time to monitor for malicious activity and performs daily scans to check for any threats that may have slipped through. If Microsoft Defender detects something suspicious, it will try to block it and alert the user. Users can also manually initiate a scan for malware at any time from the Microsoft Defender dashboard.
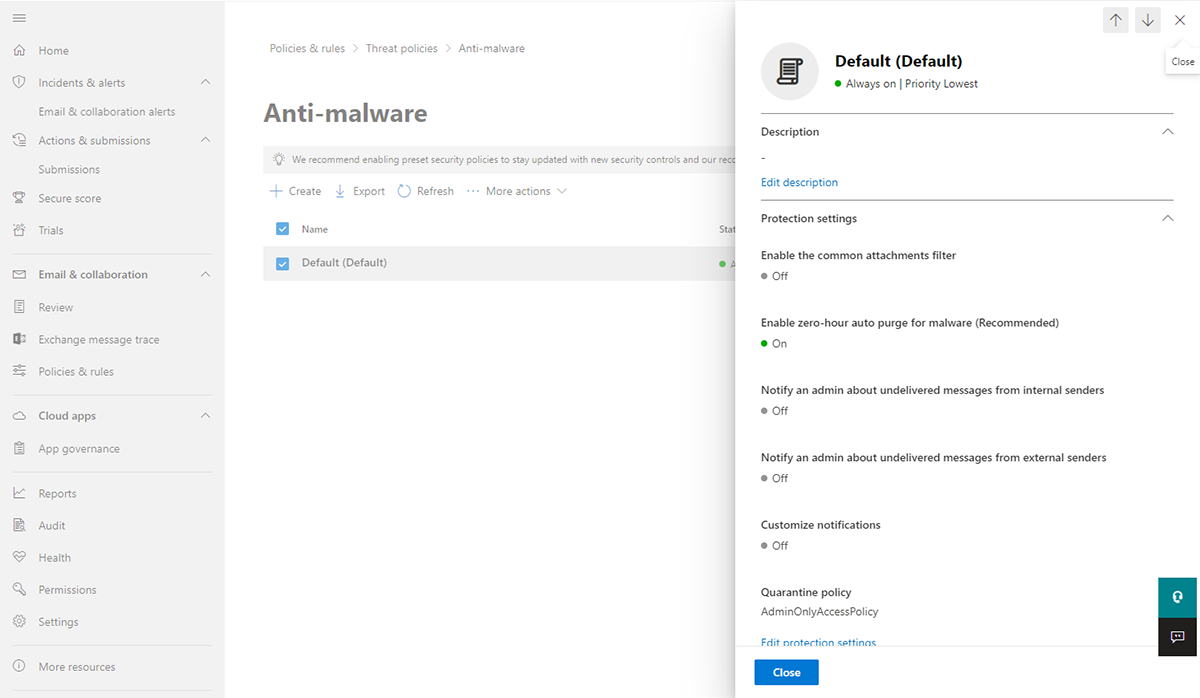
Configure Anti-malware settings
4. Address risks with Microsoft Purview
Whether threats are intentional or inadvertent, it’s vital for schools to utilize every tool and resource available to identify potential risks and close gaps before a breach occurs. Microsoft Purview Insider Risk Management helps organizations identify and address potentially risky activity by leveraging a range of service and third-party indicators. It uses logs from Microsoft 365 and Microsoft Graph to define policies for identifying risk indicators. It also provides the ability to take action to mitigate identified risks, open investigation cases, and take legal action if necessary, using eDiscovery (Premium). This tool helps schools respond to legal matters or internal investigations by identifying and collecting relevant data from the Microsoft 365 platform.
5. Manage mobile and laptop devices with Intune for Education
Intune for Education is the Microsoft 365 A5 solution for device management. In an era of Zero Trust security models, schools that reduce the number of external tools and apps students and staff use help eliminate potential insecurities and breach points. Intune for Education provides IT staff with a single platform that can manage a mix of laptops, tablets, and smartphones in multiple operating systems such as Windows, MacOS, iOS, Linux, or ChromeOS.
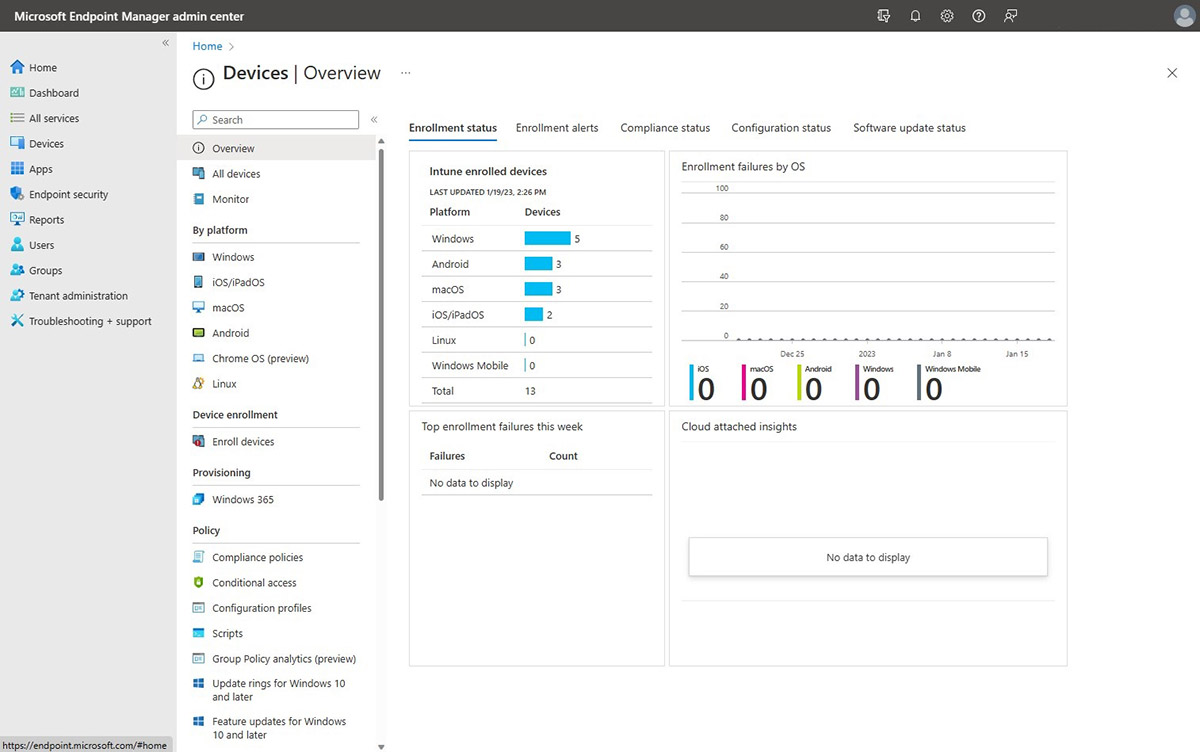
Manage your endpoint devices
IT administrators can distribute apps to students and educators without physically handling their devices. These apps become available to users the next time they log in and follow them to any device. This ensures students only have access to the instructional apps they need for learning.
Manage your endpoint apps
6. Follow legal guidelines with Compliance Manager
Compliance and security go together. By understanding and following compliance requirements, schools can better protect students and secure sensitive information. Compliance Manager in Microsoft 365 A5 provides each school with a compliance score that helps IT staff better understand their compliance posture. Schools have access to over 200 easy to use templates that simplify compliance for policies like FERPA and COPPA.
7. Archive communication with Litigation hold
With the number of users and sensitive data that schools support, there is a high chance of needing access to past email for a variety of legal purposes. Litigation hold allows IT administrators to retain all mailbox content, including deleted items and original versions of modified items, in a user's primary and archive mailboxes. IT staff can specify a hold duration for the retention of deleted and modified items or retain the content indefinitely until the hold is removed. When a Litigation hold is placed on a mailbox, deleted items and modified items are retained in the user's Recoverable Items folder for the duration of the hold. Additionally, the storage quota for the Recoverable Items folder is increased from 30 GB to 110 GB.
8. Encrypt email with Microsoft Outlook
Email is a common target for school cybersecurity attacks. In 2019, Microsoft blocked 13 billion malicious or suspicious emails. Microsoft Outlook’s protection extends to other facets of email, too, including encryption. Encrypting an email message in Microsoft Outlook converts it from readable plain text into scrambled cipher text that can only be read by someone with the private key that matches the public key used to encrypt the message. Outlook offers two encryption options: S/MIME encryption, which requires a mail application that supports the S/MIME standard, and Microsoft 365 Message Encryption (Information Rights Management). Any recipient without the corresponding private key will not be able to read the encrypted message. Through encryption, schools can keep sensitive data, such as student information, secure while still being able to share with the appropriate staff members or caregivers.
9. Save videos to a private server with Microsoft Stream
Microsoft Stream is a video server platform that helps keep content secure. The platform simplifies the process of recording Teams meetings and sharing with a group, whether that’s a class of students or one for faculty and staff members. Videos are automatically saved in OneDrive and can be shared directly within a Teams for Education class or through the share settings. By keeping files in an internal, managed setting, districts can avoid uploading videos to a public-facing video hosting platform and eliminate the need to pay for a separate district video server.
10. Protect files with Microsoft Defender Safe Documents
Students, teachers, administrators, and caregivers are constantly sending and sharing a variety of files and documents. Because of this, a single corrupted file could easily be opened and cause potential harm. Institutions that use Safe Documents can view potentially malicious files in protected view without the risk of infection. This grants users protection from harmful documents while still being able view the content. Safe Documents scans Office documents in Protected View or Application Guard for Office using the cloud backend of Microsoft Defender for Endpoint. Users can access Safe Documents protection without needing to have Defender for Endpoint installed on their local devices.
Meeting schools' unique security needs
Microsoft 365 A5 security tools help protect educational institutions from various cybersecurity threats. It includes advanced threat protection through tools like Microsoft Defender for Endpoint, mobile device management with Intune for Education, and phishing prevention with Microsoft 365 Defender. By implementing this comprehensive security solution, districts can better secure their schools and protect themselves from evolving risks.
Explore Microsoft A5 security tools to learn more about protecting against cybersecurity threats.